Quick Solutions for Reference
SECTION – A (Very Short Answers)
Q1. Define Kerberos.
- Kerberos is a centralized network authentication protocol based on secret-key cryptography using tickets.
- It allows users and services to securely prove their identity over an insecure network via a trusted KDC (Key Distribution Center).
Q2. What is worm?
- A worm is a self-replicating malware that spreads across systems automatically without user action.
- It exploits network vulnerabilities and consumes system/network resources while spreading.
Q3. What is trusted software?
- Trusted software is software that correctly enforces the system’s security policy without violating it.
- It is tested, verified, and relied upon to maintain confidentiality, integrity, and availability.
Q4. What is intruder?
- An intruder is a person or program that attempts unauthorized access to computer resources or network services.
- The goal is usually to steal information, misuse resources, or disrupt the system.
Q5. What is Zombie?
- A zombie is a compromised computer system remotely controlled by an attacker without the owner's knowledge.
- Zombies are often used in botnets for sending spam, DDoS attacks, or other malicious activities
SECTION – B (Short Answers)
Q1. List the limitations of SMTP / RFC 822.
Any 4–5 points are usually enough:
- 7-bit ASCII only – Original SMTP/RFC 822 supports only 7-bit ASCII text; cannot directly handle binary data.
- Poor support for multimedia – Images, audio, video, executables etc. cannot be sent directly; they must be encoded (e.g., base64) and handled by extensions like MIME.
- No built-in security – No encryption, integrity protection or authentication in basic SMTP; messages can be read or modified in transit.
- Limited character set – Non-English characters and many international languages are not supported in plain RFC 822.
- Line length and structure limits – Maximum line length (1000 characters) and rigid header formatting.
Q2. What are the services provided by PGP?
Pretty Good Privacy (PGP) for e-mail provides:
- Authentication – Digital signatures verify the sender and provide non-repudiation.
- Confidentiality – Encrypts the message using symmetric key, and then encrypts that key with public-key crypto.
- Compression – Message is compressed before encryption to save space and increase security.
- E-mail compatibility – Converts binary data into ASCII (radix-64) so it can pass through traditional mail systems.
- Segmentation & reassembly – Large messages are broken into smaller blocks and reassembled at the receiver.
Q3. Define S/MIME.
S/MIME (Secure/Multipurpose Internet Mail Extensions) is a security-enhanced version of the MIME email standard that uses public-key cryptography to secure email communication.
It provides strong security services such as confidentiality, authentication, message integrity and non-repudiation for electronic mails.
S/MIME supports:
- Encrypted emails – The message body is encrypted using symmetric key cryptography, and the symmetric key is further encrypted with the receiver's public key.
- Digital signatures – Ensures the authenticity of the sender and protects against modification of the message content.
- Certificate-based trust model – Uses X.509 digital certificates to verify and validate public keys.
- MIME compatibility – Supports attachments, multimedia and non-ASCII characters, making it usable across different mail systems without formatting issues.
- Interoperability – Works across major email clients (Outlook, Thunderbird, etc.) and mail servers, enabling secure message exchange between different platforms.
SECTION – C (Descriptive Answers)
You have to attempt any one in exam.
(a) Explain the architecture of IP Security (IPsec).
IPsec is a suite of protocols that provides security at the network layer (IP layer) so that all upper-layer protocols (TCP, UDP, etc.) can be protected transparently.
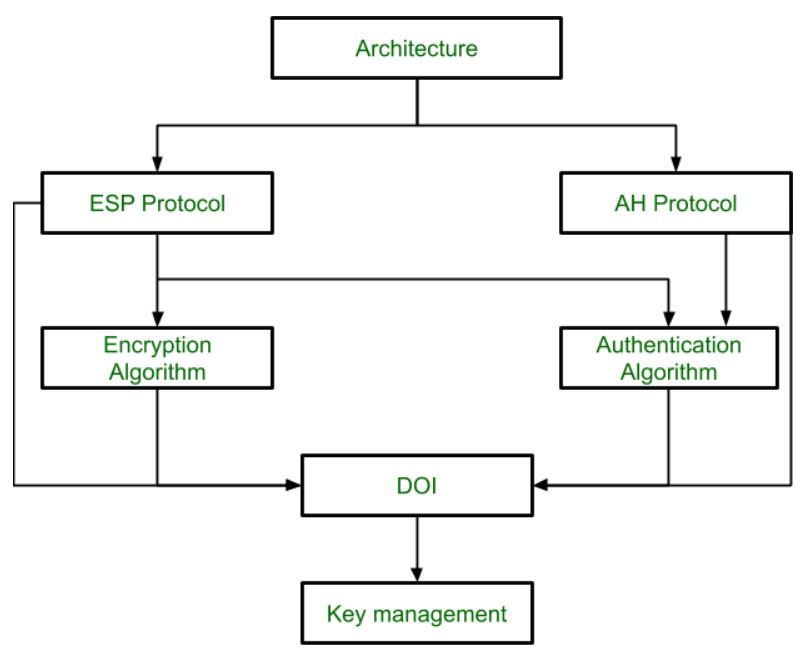
Main components of IPsec architecture:
1. Security Associations (SAs): A Security Association is a unidirectional logical connection that defines how traffic will be protected.
Each SA specifies:
- Security protocol used (AH or ESP)
- Encryption and/or authentication algorithms and keys
- Lifetime and sequence number state
- Identified by SPI (Security Parameters Index) + destination IP + protocol (AH/ESP).
2. Protocols: AH and ESP
- AH (Authentication Header)
- Provides data origin authentication, connectionless integrity and anti-replay protection.
- Does not provide confidentiality (no encryption).
- ESP (Encapsulating Security Payload)
- Provides confidentiality by encrypting the payload.
- Can also provide integrity, authentication and anti-replay (optional authentication field).
3. Modes of Operation
- Transport Mode
- Protects only the payload of the IP packet (upper-layer data); original IP header remains.
- Typically used for end-to-end host-to-host security.
- Tunnel Mode
- Entire original IP packet (header + payload) is encrypted/authenticated and encapsulated inside a new IP packet.
- Commonly used between security gateways (e.g., between two firewalls in a VPN).
4. Key Management – IKE (Internet Key Exchange)
- IPsec relies on IKE to automatically establish SAs, authenticate peers and negotiate cryptographic algorithms/keys.
- Works in phases (e.g., IKE SA setup, then IPsec SA setup).
5. Security Policy Database (SPD)
- Contains rules that determine which packets must be protected with IPsec (and how), which can bypass IPsec, and which must be discarded.
- For each outbound packet, SPD is consulted to select appropriate SA or action.
Summary:
In the IPsec architecture, outgoing packets are checked against the SPD, mapped to an SA, then processed by AH/ESP (in transport or tunnel mode) using keys negotiated by IKE. Incoming packets are processed in reverse order, verified with the corresponding SA, and only then delivered to upper layers. This provides a secure VPN-like mechanism at the IP layer.
(b) Write short notes on Authentication Header (AH) and ESP.
1. Authentication Header (AH)
- AH is an IPsec protocol that provides:
- Data origin authentication (verifies the sender).
- Connectionless integrity (detects any modification).
- Anti-replay protection (using sequence numbers).
- It does not encrypt the data; no confidentiality.
- AH is inserted between the IP header and the upper-layer protocol (or before an ESP header).
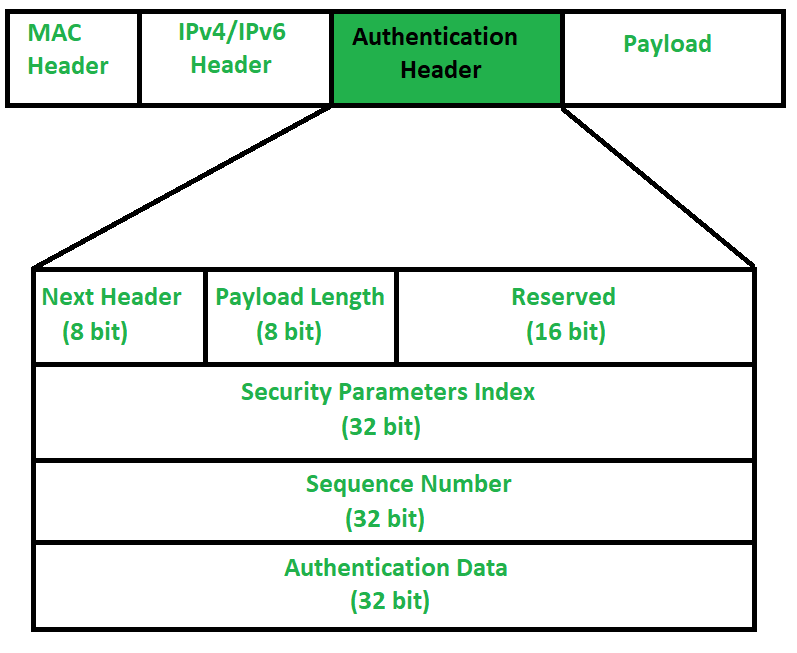
Main fields of AH (simplified):
- Next Header – Identifies the type of payload (e.g., TCP, UDP).
- Payload Length – Length of AH in 32-bit words.
- SPI (Security Parameters Index) – Points to the SA.
- Sequence Number – Increases with each packet; used for anti-replay.
- Authentication Data – Integrity Check Value (ICV), typically an HMAC over immutable parts of the IP packet and AH.
- AH protects as much of the IP header as possible plus the payload against modification.
---
2. Encapsulating Security Payload (ESP)
- ESP is the other main IPsec protocol. It provides:
- Confidentiality by encrypting the payload.
- Optional integrity and authentication of the payload and selected parts of ESP header.
- Anti-replay protection via sequence numbers (when used with an SA).
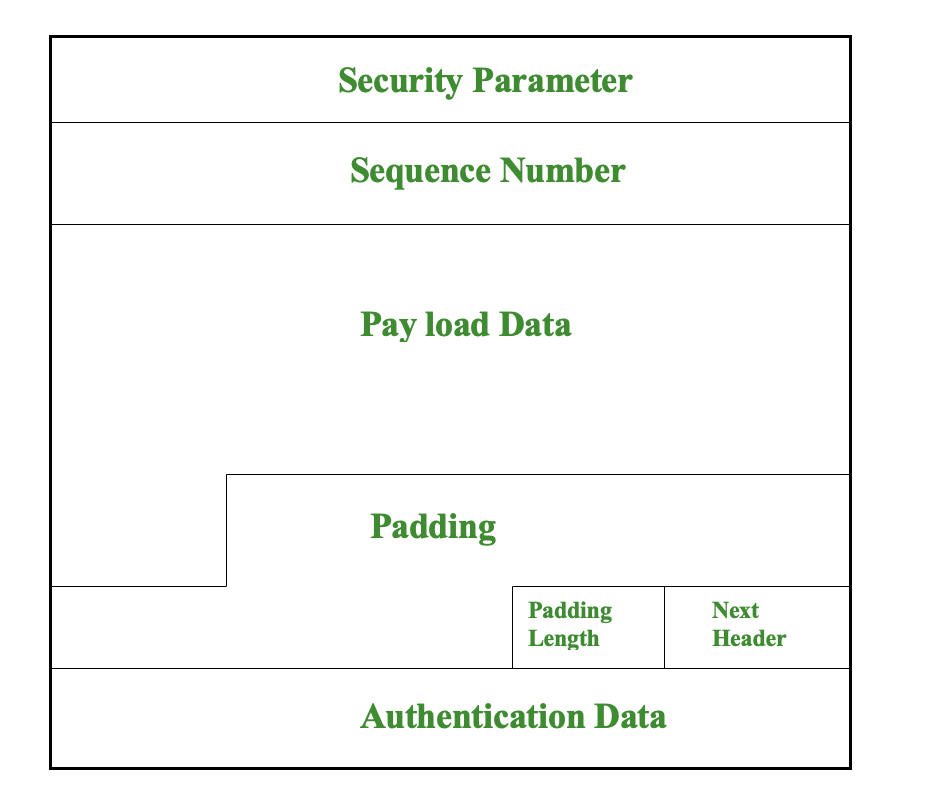
ESP packet format (simplified):
- ESP Header:
- SPI
- Sequence Number
- Payload Data:
- Encrypted upper-layer protocol data (and possibly inner IP header in tunnel mode).
- Padding, Pad Length, Next Header:
- Used to align encryption blocks and indicate the type of encapsulated data.
- ESP Authentication Data (optional):
- Integrity Check Value (ICV) over ESP header and ciphertext.
- ESP can operate in transport mode (encrypts just the transport-layer payload) or tunnel mode (encrypts the entire original IP packet), making it the main building block for VPN tunnels.